If you manage a medical practice, you've likely heard about the Change Healthcare cyberattack in early 2024. Change Healthcare processes about 40% of all medical claims in the country, and the breach potentially exposed patient data for up to a third of Americans.
This devastating attack has many practice managers wondering—Is the cloud inherently unsafe?
The good news is that cloud technology itself isn't the problem.
The real risk stems from inadequate security measures. Your practice can safely leverage the cloud—you just need the right strategies to protect your patients' data.
Let's explore what this means for your practice.
At PEAKE, we offer a secure, scalable, and compliant hosting solution specifically designed for healthcare applications, including EMR systems.
PEAKE Private Cloud addresses the limitations of on-site servers, providing a reliable alternative that supports excellent, uninterrupted patient care. Schedule a conversation today to learn more.
The Basics of Cloud Security

At its core, cloud computing provides on-demand access to a shared pool of configurable computing resources. In healthcare, these resources may include everything from electronic health records (EHR) systems to medical imaging storage and analysis tools.
Cloud services are essentially a secure digital storage facility for your practice.
Think of cloud services as a secure digital storage facility for your practice. Instead of keeping patient records and practice management tools on in-house computers, you store them in highly secure data centers.
This allows your staff to securely access practice systems from anywhere—the front desk, an exam room, or even while working remotely (with the right security measures in place, of course).
The OSI (Open Systems Interconnection) Model and Shared Responsibility
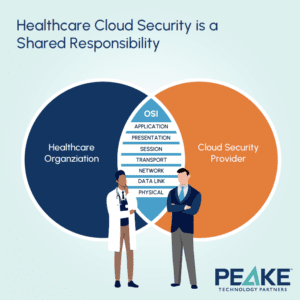
Your practice's technology systems function in multiple layers, each needing its own type of security. The OSI model defines seven layers of computing systems, from the physical layer (hardware) to the application layer (software that end-users interact with).
Each layer requires specific security considerations, regardless of whether the system is on-premises or in the cloud.
Cloud security operates on a shared responsibility model.
It's a partnership between your cloud provider and your practice. Here's how it typically works:
Provider Responsibility:
- Physical security of servers
- Network infrastructure
- Basic system security
Your Practice's Responsibility:
- Patient data protection
- Staff login credentials
- HIPAA compliance
- Access controls
Remember, your practice holds the ultimate responsibility for patient data security. Partnering with a reliable healthcare IT MSP like Peake Technology Partners can significantly strengthen your security posture and ensure compliance.
How Safe Are Cloud Services from Hackers?
Cloud services are as safe as the security measures you and your provider put in place together.
Whether your patient records are stored on computers in your office or the cloud, they need protection. The security basics are the same. Just like you need locked doors, security cameras, and staff protocols for a physical office, you need digital security measures for your cloud systems.
The advantage of the cloud is the partnership with a security team. Your cloud provider handles the heavy lifting of infrastructure security (like maintaining secure servers and preventing network attacks). Your practice focuses on day-to-day security practices like managing staff logins and protecting patient data.
You need both parts working well—your provider's security systems and your practice's careful data handling—to keep patient information secure.
Fundamental Cloud Security Considerations for Medical Practices
When protecting patient data in the cloud, focus on these three key areas:
1. Manage Who Has Access to What
Set up role-based access to ensure staff can only access what they need and multi-factor authentication for an extra layer of security.
2. Protect Your Data
Keep regular, secure backups so that data can be recovered in case of system failures or ransom attacks. Ensure you have backup plans so your practice will be able to function and see patients if your systems go down.
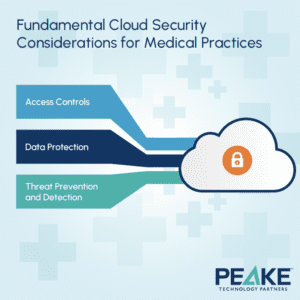
3. Threat Prevention and Detection
Along with real-time threat monitoring, explore intrusion prevention systems (IPS) and intrusion detection systems (IDS). These systems scan and analyze network traffic, blocking threats and alerting security when threats are detected.
Focusing on these key areas can significantly enhance your practice’s cloud security. While your organization is responsible for implementing these practices, your cloud provider is crucial in supporting and enabling them.
For detailed guidance on selecting the right cloud security provider for your healthcare organization, read our article: A Practice Manager’s Guide to Choosing the Right Healthcare Cloud Provider.



